Featured SRI PhD Project

Enhancing Cyber Attack Prevention and Detection using Application Process Tracing
Nowadays, software enterprises are being targeted by more advanced cyber-security threat models. Consequently, more sophisticated means of protecting software organisations are in high demand. Also, microservices are trending for being amongst the most popular software application design architecture. The aim of this thesis is to explore how application process tracing can be applied to enhance cyber-attack prevention and detection.
OBJECTIVES
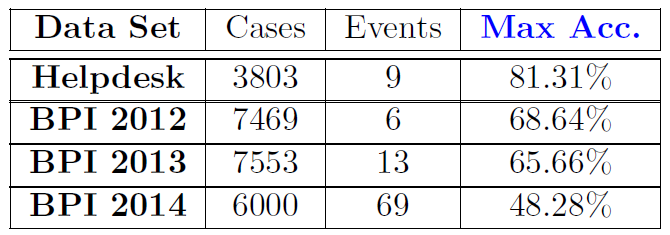
We propose two objectives for this research. The first objective is to observe how the prediction of future events in an application thread can help identify potential targets and thus enable cyber-security personnel to take proactive defensive measures. This approach is valid for general business application processes. The second objective is to investigate how anomaly detection approaches can be applied to microservice application process tracing and detect seeded cyber-attacks.
Approach 1.
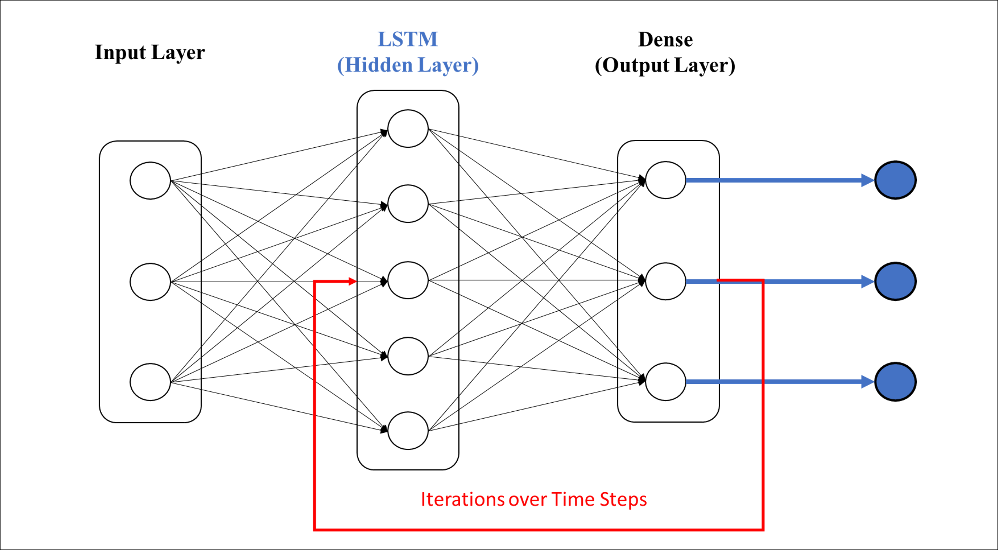
One approach for addressing the first objective is to employ a machine learning model to learn general business application processes and functionality to provide a contextual oversight of the application’s infrastructure. This can be done by applying process mining to observe the execution paths of application processes. An alternative method is to employ a deep learning model to discover the contextual oversight of the application process. We trained a LSTM model to learn the sequential dependencies for existing processes and subsequently made predictions in ongoing process instances.
Approach 2.
For addressing our second objective, we considered microservice application process tracing. The functionality of a microservices application can be monitored and logged using distributed tracing. Anomaly detection is defined as the discovery of irregular instances or patterns within a data series. To enhance detection of cyber-attacks, frequency distribution-based anomaly detection was performed to identify anomalous trace activity within a synthetic data set of traces. This machine learning model was tested by simulating a brute force password guessing attack against the application.
Part 2 of Thesis:
An open-source microservices application, SocialNetwork is run and general traffic is generated and logged using distributed tracing. A brute force password attack cyber-attack is seeded and detected using frequency analysis-based anomaly detection.

Part 3 of Thesis:
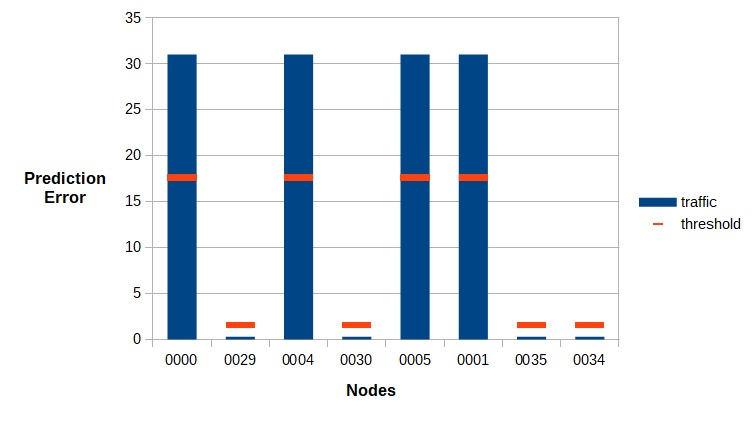
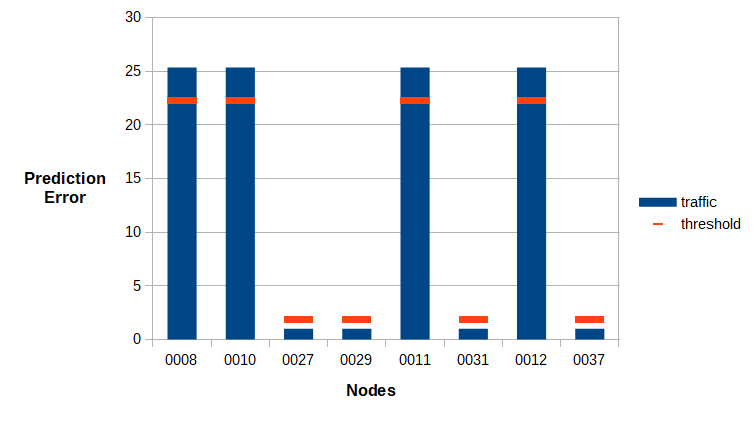
The microservices application is runs again for this project, microservice traffic is generated, a graph convolutional neural network, the DCRNN model, is trained to discover the spatial and temporal dependencies of the data and threshold-based anomaly detection is performed detect seeded cyber-attacks based on anomalous microservices traffic.